

In today’s digital landscape, cybersecurity threats are evolving rapidly, posing significant risks to businesses of all sizes. According to the Verizon Data Breach Investigations Report (DBIR), there were over 23,000 security incidents reported globally in 2023, with 5,200 confirmed data breaches. Additionally, research from Cybersecurity Ventures predicts that cybercrime will cost the world $10.5 trillion annually by 2025 — a massive increase from $3 trillion in 2015. Organizations of all sizes are vulnerable, with ransomware, phishing, and insider threats ranking among the most prevalent attack vectors.
With the increased adoption of cloud computing, IoT devices, and remote work models, businesses are becoming more complex and interconnected, further expanding their attack surfaces. Consequently, IT departments are under increasing pressure to adopt proactive strategies that improve security processes. Continuous Improvement (CI) methodologies offer a structured framework for enhancing cybersecurity strategies through iterative enhancements, data-driven decisions, and automation. This white paper outlines how CI principles can strengthen cybersecurity defenses and outlines an actionable plan for implementation.
Jump to read how continuous improvement methodologies can help:
Cybersecurity risks are growing at an unprecedented pace, with organizations facing thousands of potential threats each day. Regular risk assessment is essential to identifying vulnerabilities before they can be exploited. Continuous Improvement (CI) tools provide IT teams with proactive strategies to identify and mitigate risks effectively.
Kaizen events—focused, short-term, cross-functional improvement workshops—are traditionally used in lean manufacturing and operations, but they can be effectively adapted to help companies identify and assess cybersecurity risks. Here’s how:
Rapid Cross-Functional Risk Identification
Kaizen events bring together people from different departments (IT, operations, HR, legal, etc.) to evaluate processes end-to-end. This collaboration:
Process Mapping to Reveal Weaknesses
Using tools like Value Stream Mapping (VSM) or process flow diagrams, a Kaizen team can:
Visualize how data is stored, accessed, and transmitted.
Identify security gaps at each process step, such as unsecured file sharing, outdated software, or lack of authentication.
Root Cause Analysis of Past Incidents
A cybersecurity-focused Kaizen can include analysis of recent threats or breaches:
Using 5 Whys or Fishbone Diagrams to identify underlying causes (e.g., insufficient training, weak passwords, no patch management).
Creating action plans to prevent recurrence.
Establishing Quick Wins and Long-Term Controls
Kaizen events emphasize immediate, actionable improvements, which can include:
Implementing multi-factor authentication.
Updating firewall rules or user permissions. Launching cybersecurity awareness training.
Larger gaps identified (e.g., legacy systems with vulnerabilities) are documented for longer-term investment and remediation.
Building a Culture of Cyber Awareness
By involving non-technical teams, Kaizen events help:
Spread cybersecurity accountability beyond the IT department. Increase awareness and vigilance throughout the organization.
Establish a repeatable framework for cybersecurity reviews—embedding cybersecurity into continuous improvement and making it a recurring activity instead of a one-off.
Case Study: Kaizens Improve Profitability
A specialty gift basket franchise faced operational strain from order surges, losing sales due to limited capacity and inefficient custom order handling. Adonis Partners’ experts conducted assessments, mapped processes, and led Kaizen sessions, identifying 30 distinct improvement opportunities and resulting in a scalable, more profitable operating model.
Using Plan-Do-Check-Act (PDCA), companies can treat cybersecurity not as a one-time project, but as an ongoing cycle of improvement— allowing for systematic identification, assessment, and mitigation of risk in a way that adapts to changing threats and technologies.
Plan – Identify Risks and Define Controls
Assess current cybersecurity posture: Inventory assets, map data flows, and identify potential vulnerabilities.
Identify risk scenarios: Consider insider threats, phishing, ransomware, third-party access, etc.
Set objectives and controls: Define acceptable risk levels, compliance needs (e.g., ISO 27001, NIST), and mitigation strategies.
Plan assessments: Develop plans for penetration testing, vulnerability scans, and training.
Do – Implement Controls and Execute the Plan
Roll out technical controls (firewalls, MFA, encryption), governance measures (policies, access rights), and human safeguards (training, simulated phishing).
Conduct risk assessments, audits, or tabletop exercises.
Begin data collection (incident logs, access records, system alerts).
Check – Monitor and Evaluate Risk Exposure
Analyze logs and incident data to spot trends or anomalies.
Evaluate control effectiveness: Are systems being patched? Are phishing attempts succeeding?
Use audits or internal reviews to assess compliance with security policies.
Act – Improve and Strengthen Security Posture
Address gaps revealed in the “Check” phase: update policies, retrain staff, revise controls.
Adjust risk assessments and objectives based on new threats or incidents. Share lessons learned and institutionalize best practices.
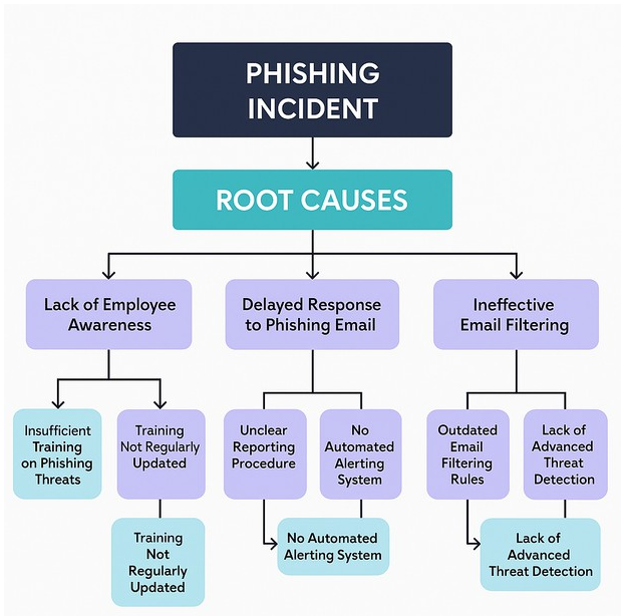
Root Cause Analysis (RCA) is a structured method used to uncover the underlying causes of problems. Rather than just addressing symptoms (e.g., a data breach or malware infection), RCA helps organizations understand why they occurred, so they can prevent future occurrences.
Incident Investigation
When a cybersecurity event happens, RCA enables a deep dive into:
Tools like the “5 Whys” or Fishbone Diagrams help trace the event to its root.
Identify Systemic Weaknesses
RCA reveals underlying vulnerabilities, such as:
These findings guide risk assessments by showing where controls are missing or ineffective.
Improve Risk Assessments
By understanding patterns of failure through RCA, organizations can:
RCA turns one incident into a learning opportunity for broader risk prevention.
Strengthen Controls and Processes
RCA informs actionable improvements:
This closes the loop between incident response and long-term cybersecurity resilience.
With cyberattacks increasing in frequency and complexity, delays in responding to security incidents can have devastating consequences. CI methodologies help IT teams improve their response processes to minimize disruption and data loss.
The Improve phase of Lean Six Sigma can help organizations implement targeted solutions to remove waste, reduce variation, and enhance response speed and accuracy.
Eliminate Non-Value-Added Steps (Lean Focus)
Standardize Incident Response Workflows
Automate Repetitive and Error-Prone Tasks
Enhance Team Collaboration and Handoff Efficiency
Pilot and Test the New Process
Implement Visual Management and Real-Time Monitoring
Quick wins with Lean Six Sigma in Cybersecurity:
With organizations processing vast amounts of data daily, threats can easily go unnoticed. Continuous monitoring powered by CI tools enhances visibility and ensures security teams can detect and mitigate risks before they escalate.
Kanban’s strength lies in visualizing work, limiting work in progress, and improving flow—all critical to handling dynamic, high-volume threat data. Applied to cybersecurity, Kanban can make threat detection processes more transparent, responsive, and resilient.
Visualize the Threat Monitoring Process
Benefit: Security teams can instantly see the status of every threat, identify bottlenecks, and prioritize the most critical alerts.
Prioritize Threats Based on Severity
Benefit: Ensures that serious threats are addressed quickly and lower-risk issues are not overlooked.
Limit Work in Progress (WIP) to Avoid Alert Fatigue
Benefit: Maintains focus, reduces errors, and improves the quality of detection and analysis.
Enable Real-Time Collaboration and Accountability
Benefit: Reduces miscommunication and ensures faster handoffs across detection, triage, and response teams.
Monitor Performance and Flow Over Time
Benefit: Drives continuous improvement in threat detection and incident handling.
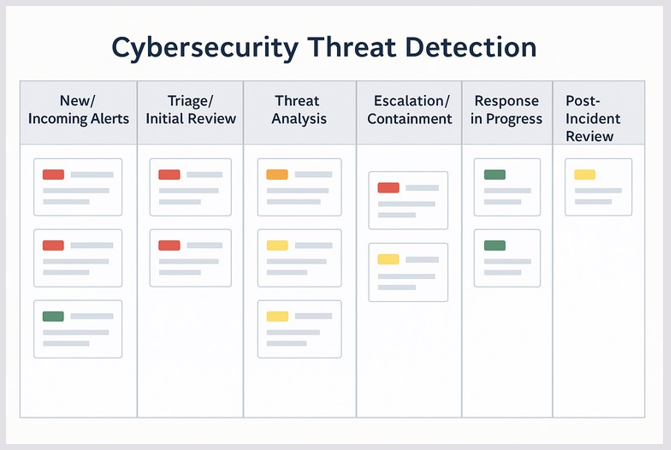
Kanban Card Elements
Each alert or incident is a Kanban card, which can include:
Agile enables a dynamic, fast-moving, and responsive approach to cybersecurity threat detection. By focusing on iteration, collaboration, and continuous delivery, organizations can stay ahead of evolving threats while improving detection quality and speed.
Iterative Improvement of Detection Capabilities
Example: Updating SIEM correlation rules or deploying a new anomaly detection algorithm every two weeks.
Real-Time Collaboration and Feedback Loops
Example: Analysts surface recurring false positives during standups, prompting rule tuning within the same sprint.
Adaptive Response to Emerging Threats
Example: A new zero-day vulnerability is discovered—team allocates sprint capacity to build detection and alerting for it immediately.
Continuous Integration of Security Tools
Example: Adding cloud workload protection monitoring across environments one team or region at a time, evaluating performance as you go.
Measurable Progress and Transparency
Example: The team sees that detection tuning tasks are often blocked due to lack of log visibility and prioritizes log ingestion improvements.
Embedding Threat Detection in DevSecOps
Example: Security engineers push updates to detection policies via version control and track effectiveness like software code.
Quick wins with Agile in Cybersecurity:
Phishing, social engineering, and human error are among the leading causes of data breaches. CI-driven training strategies ensure employees are continuously educated and prepared to recognize these threats.
Kaizen transforms cybersecurity awareness from a once-a-year requirement into a daily, team-driven mindset. By focusing on continuous, employee-led improvements, organizations create a culture where secure behavior is second nature—and constantly getting better.
Empowers Employees to Own Cybersecurity: Kaizen encourages bottom-up participation, giving employees a role in identifying security gaps in daily behaviors and suggesting improvements. This builds accountability and makes cybersecurity feel like everyone’s job—not just IT’s.
Identifies Real-World Training Needs: Through Kaizen workshops, Gemba walks, or team discussions, managers can uncover where employees are confused, undertrained, or using workarounds that introduce risk. This leads to targeted, relevant training, rather than generic or compliance-based sessions.
Reinforces Continuous Learning: Rather than one-time annual training, Kaizen supports ongoing, incremental learning. Short refresher modules, feedback loops, and micro- trainings can be introduced as part of regular work.
Encourages Process and Habit Improvements: Kaizen looks at how daily work is done— perfect for refining secure behaviors like locking screens, reporting suspicious emails, or managing access credentials. Teams can propose and adopt “security best practices” through their own process improvements.
Creates a Feedback-Driven Culture: Kaizen events open space for employees to provide real-time feedback on what’s working in training—and what isn’t. Training can be adjusted based on effectiveness, participation, and actual behavior changes.
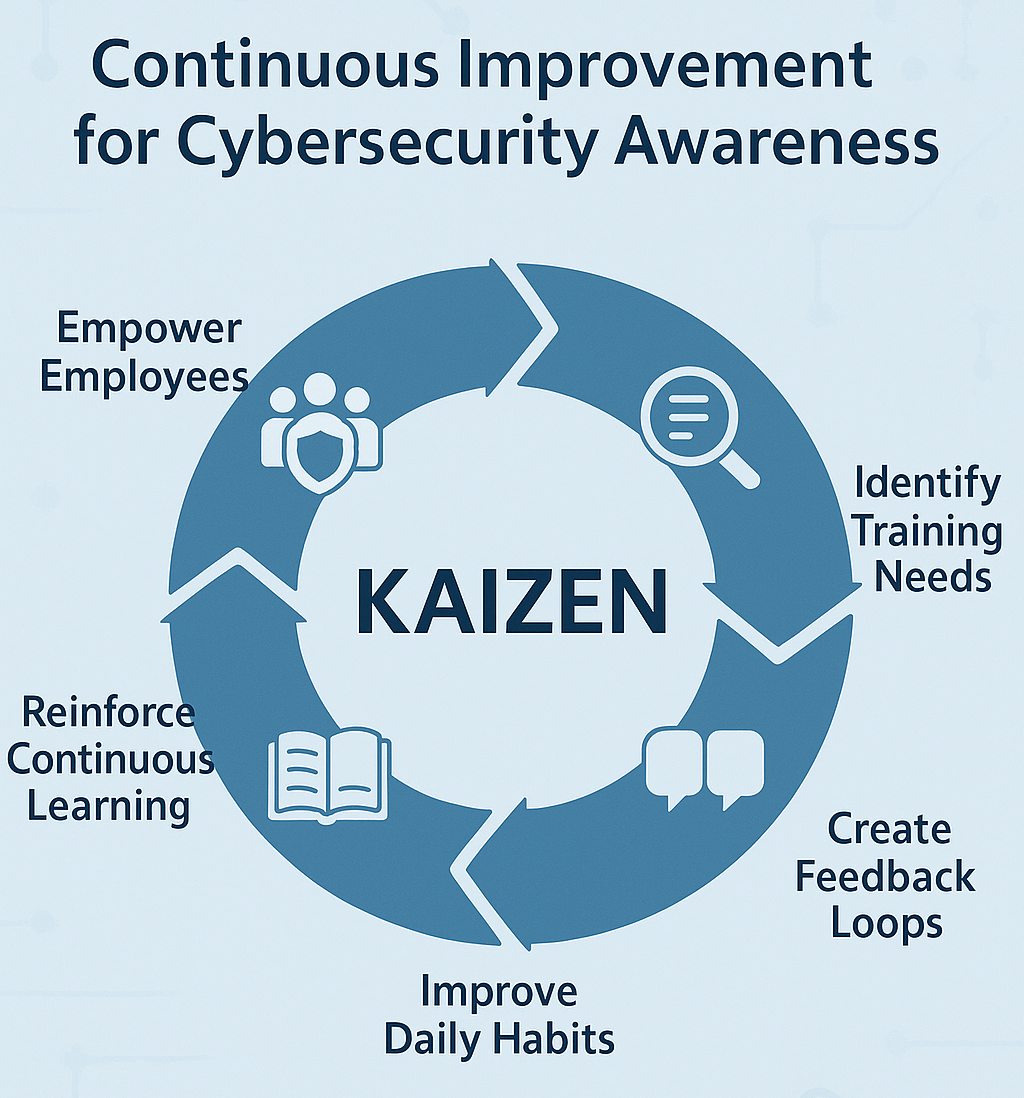
Standard Work Practices provide the foundation for a secure workforce by clearly defining and reinforcing secure behaviors. They ensure training is relevant, reduce risk from inconsistency, and make it easier to audit, improve, and scale cybersecurity awareness over time.
Establishes Clear Expectations for Secure Behavior: Standard Work documents the baseline for secure practices—such as how to handle sensitive data, manage passwords, report suspicious activity, or use email securely. This reduces ambiguity and ensures every employee knows exactly what “secure” looks like in daily work.
Enables Consistent, Role-Based Training: Training programs can be customized based on the Standard Work for each role or department. Employees get relevant, practical training tied to their daily responsibilities— making it easier to apply and retain.
Reduces Risk from Inconsistent Practices: Without Standard Work, cybersecurity practices vary by person or team—leading to gaps and vulnerabilities. Standardizing processes helps ensure consistent risk mitigation across departments.
Supports Ongoing Reinforcement and Auditing: Once in place, Standard Work can be audited and reviewed regularly to ensure adherence and identify opportunities for updates. It also enables peer-to-peer coaching, as experienced employees help newer ones follow the same secure procedures.
Makes Continuous Improvement Easier: Standard Work serves as a baseline for improvement—if a security breach or training gap is discovered, teams can quickly update procedures and retrain. New best practices can be documented and deployed across the organization quickly.
Case Study: Standardizing to Improve Quality
In 8 weeks, Adonis Partners helped a loyalty marketing company improve IT and operational quality by conducting 20+ SME interviews, identifying 28+ improvement opportunities, and standardizing code reviews, QA practices, and campaign processes.
Patch management is a crucial yet often overlooked component of cybersecurity. Outdated software remains one of the most common entry points for cyberattacks. CI methodologies help IT teams refine patching processes for improved efficiency and security.
DMAIC helps organizations transform patch management from a reactive, fragmented task into a proactive, streamlined, and measurable process. The result is stronger cybersecurity, reduced exposure to known threats, and greater confidence in system resilience.
Define – Clarify the Problem and Goals
Measure – Collect Baseline Data
Track current metrics like:
Quantifying the current state reveals both risk exposure and operational inefficiencies.
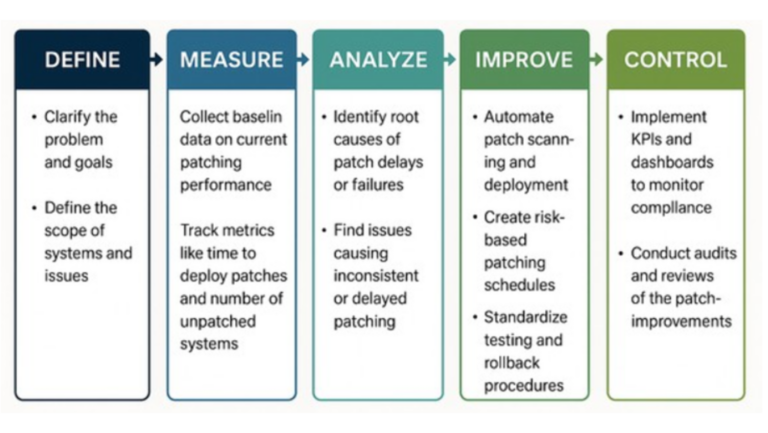
Analyze – Identify Root Causes of Patch Delays or Failures
Use tools like Fishbone Diagrams or 5 Whys to pinpoint issues such as:
This phase identifies why patches are delayed or missed—and what’s causing system instability post-update.
Improve – Design and Implement Process Enhancements
Focus on faster response, higher patch coverage, and fewer errors.
Control – Sustain the Improvements
Implement KPIs and dashboards to monitor patch status and compliance continuously.
This ensures the improved patching process stays on track and adapts as systems grow.
As businesses scale, IT teams face increasing workloads managing repetitive security tasks such as log reviews, firewall updates, and patch management. Automation through CI practices ensures these tasks are performed accurately and efficiently.
Lean automation empowers security teams to do more with less— minimizing waste, standardizing execution, and automating repetitive tasks with precision. The result is a faster, more scalable, and more resilient cybersecurity operation.
Identifies and Eliminates Wasteful Security Tasks
Lean focuses on removing non-value-added steps in security workflows. By mapping processes (e.g., threat detection to ticket resolution), teams can spot tasks that are manual, slow, or duplicated—and target them for automation. Example: Manually checking for failed logins across systems is replaced with a rule-based alert.
Automates Routine, High-Volume Activities
Common repetitive tasks that can be automated using SOAR (Security Orchestration, Automation, and Response) or RPA (Robotic Process Automation) include:
Standardizes Responses for Common Threats
Lean automation supports repeatable workflows for known scenarios (e.g., suspected malware, endpoint anomalies). Automating playbooks ensures consistency, reduces time to respond, and limits reliance on tribal knowledge. Example: If an endpoint triggers a known malware signature, the system auto-isolates the device, notifies the user, and opens an incident ticket.
Integrates Tools for End-to-End Flow
Lean automation connects disparate systems (SIEM, ticketing, firewall, EDR, IAM) into seamless workflows, eliminating siloed efforts. APIs and automation scripts ensure alerts move efficiently through detection, analysis, and resolution. Example: An alert from the SIEM triggers an auto-enrichment from a threat intel source and sends key details to Slack and ServiceNow.
Reduces Human Error and Improves Accuracy
Manual processes often lead to inconsistent responses, missed alerts, or misconfigurations. Automation ensures faster, more reliable execution of repetitive security steps. Example: Credential revocation upon employee offboarding is automated to prevent access gaps.
Enables Continuous Improvement
Lean promotes ongoing evaluation of automated workflows to ensure they’re aligned with evolving threats and business needs. Regular review of performance data (false positives, time savings, etc.) helps optimize further. Example: Weekly review of automation logs identifies redundant steps or opportunities to further tune logic.
Process optimization turns repetitive, error-prone security tasks into efficient, automated workflows. By analyzing, simplifying, and standardizing key processes, organizations can scale their cybersecurity operations while freeing up skilled personnel for more strategic work.
Maps and Analyzes Current Security Workflows
Start by visualizing end-to-end processes using Value Stream Mapping or Swimlane Diagrams. Identify where tasks are:
Standardizes Security Tasks for Automation
Once optimized, tasks are documented with clear steps, roles, and logic—making them ready for automation tools like SOAR or RPA. Consistency is key: automation only works if the process is predictable and standardized. Example: A standardized process for terminating user access is optimized for timing and handed off to an automation script.
Prioritizes High-Impact Automation Opportunities
Use Pareto Analysis or ROI evaluation to prioritize which repetitive tasks to automate first. Focus on tasks that:
Reduces Hand-Offs and Friction Between Teams
Less back-and-forth = faster execution and fewer dropped tasks. Example: Automating data sharing between SIEM and ticketing systems cuts down on manual re-entry and improves response times.
Enables Continuous Monitoring and Improvement
With optimized workflows in place, teams can implement dashboards and metrics to monitor task performance and identify further refinement opportunities. Feedback loops ensure automated processes evolve with the threat landscape. Example: An auto- quarantine process for phishing emails is monitored weekly for false positive rates and adjusted accordingly.
Case Study: 100% On-time Performance
An aerospace manufacturer faced system adoption and data accuracy challenges at a new production site with advanced, unfamiliar processes. Adonis Partners’ experts identified root causes, implemented a structured data and accountability framework, and within months, stabilized operations— achieving 100% on-time performance, and eliminating supplier shortages.
Data is vital in cybersecurity decision-making, yet many organizations struggle to effectively collect and analyze security data. CI methodologies enable IT teams to extract meaningful insights from metrics and improve security processes.
KPI tracking empowers cybersecurity teams to act with precision, prioritize intelligently, and continuously improve. It turns raw data into strategic insight, helping organizations strengthen defenses with confidence and clarity.
Quantifies Security Performance
KPIs convert cybersecurity efforts into tangible metrics that can be monitored and compared over time. These metrics tell you what’s working, what’s not, and where to focus resources. Examples include:
Enables Proactive Risk Management
Regular tracking highlights trends and anomalies before they become critical issues. Organizations can forecast risk exposure, spot emerging threats, and prioritize mitigation strategies based on evidence.
Drives Accountability Across Teams
KPIs help assign ownership and responsibility for specific security outcomes. They clarify expectations and allow performance comparisons across teams, sites, or departments.
Supports Executive Communication and Investment
Leadership needs clear, quantifiable indicators to support cybersecurity funding and strategic decisions. KPIs translate complex security data into simple dashboards and trendlines to facilitate decision making.
Facilitates Continuous Improvement
By reviewing KPIs in regular cadence meetings (weekly, monthly, quarterly), teams can iteratively improve. Underperforming KPIs signal where to audit processes, train staff, or enhance tooling.
Root Cause Analysis empowers organizations to make smarter cybersecurity decisions by exposing the real reasons behind security failures. With better insight comes better action—leading to reduced risk, stronger resilience, and more efficient use of security resources.
Transforms Incidents Into Actionable Insights
RCA helps convert breach reports, incident logs, or audit findings into structured learning opportunities. By understanding what really went wrong—not just what happened— organizations can make informed, targeted decisions.
Identifies Systemic Weaknesses Across Teams and Tools
RCA brings data from multiple sources—SIEM logs, user reports, endpoint data—into a single analysis. This cross-functional visibility exposes patterns and recurring failures, supporting long-term improvements across people, processes, and technologies.
Prioritizes Investments Based on Evidence
RCA findings inform strategic decisions about where to invest in controls, automation, or training. Leaders can justify cybersecurity budgets based on quantifiable root causes rather than guesswork.
Drives Continuous Improvement Loops
RCA fits naturally into post-incident reviews, enabling iterative refinement of detection, prevention, and response processes. Organizations build a culture of evidence-based decision making—learning from every incident to reduce future risk.
Improves Accountability and Knowledge Sharing
RCA encourages documentation of decisions and outcomes, allowing teams to track improvements and prevent repeat mistakes. It also fosters organizational learning, creating a shared understanding of what needs to change and why.
Cyber threats are constantly evolving, requiring organizations to adopt a proactive and adaptive mindset. Establishing a culture of Continuous Improvement ensures that IT teams are always prepared to refine and enhance security protocols.
Kaizen fosters a proactive, people-powered approach to cybersecurity—turning everyday actions into continuous progress. By embedding improvement into daily routines, organizations build a culture where cybersecurity isn’t just reactive—it’s always evolving.
Empowers Employees to Own Cybersecurity
Kaizen encourages bottom-up involvement, making every employee a participant in identifying and improving security practices. Security becomes a shared responsibility, not just the domain of IT.
Facilitates Regular, Low-Cost Security Improvements
Instead of waiting for large initiatives, Kaizen enables small, actionable changes through quick cycles. This agility helps teams respond to evolving cyber threats without major overhauls.
Makes Cybersecurity More Visible and Measurable
Kaizen events often use visual tools (like boards, metrics, and root cause diagrams) to highlight issues and progress. Teams track cybersecurity performance and improvements over time, reinforcing accountability.
Encourages Cross-Functional Collaboration
Kaizen brings together diverse roles—security analysts, IT, operations, HR—to solve problems holistically. This helps bridge silos and ensures that cybersecurity is integrated across business processes.
Drives Ongoing Training and Awareness
Kaizen promotes a mindset of learning by doing, ideal for reinforcing secure behaviors and procedures. It encourages continuous review of training programs based on real- world feedback.
Builds a Scalable Improvement Framework
Once established, Kaizen can be embedded into regular security operations—weekly huddles, monthly improvements, quarterly strategy reviews. It evolves into a living system of security enhancement that scales with the organization.
Gemba walks embed cybersecurity into the daily rhythm of the organization—turning observation into insight, and insight into action. By going to where the work happens, organizations foster a grounded, people-centered culture of continuous security improvement.
Brings Visibility to Day-to-Day Cybersecurity Practices
Leaders and security teams observe how security policies are implemented across departments, systems, and user behaviors. This reveals gaps, workarounds, and real-time challenges that might be missed in reports.
Encourages Open Dialogue Between Teams
Gemba walks promote nonjudgmental, collaborative conversations about cybersecurity practices. Frontline employees feel heard, and leadership gains trust by engaging directly with teams.
Identifies Misalignments Between Policy and Reality
Observing workflows in context helps spot where policies are impractical, outdated, or ignored. These insights drive smarter, more tailored improvements that reflect how people actually work.
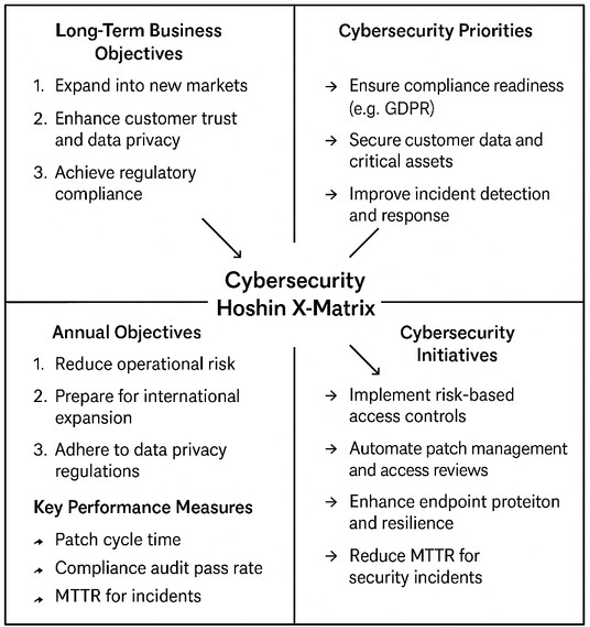
Cybersecurity efforts must align with business goals to ensure strategic resilience and long-term success. CI tools help IT leaders integrate security objectives into broader business priorities for improved alignment and outcomes.
Hoshin Kanri helps organizations elevate cybersecurity from a technical function to a strategic enabler. By tightly aligning strategies with business objectives, companies can ensure focused execution, stronger risk management, and measurable growth, trust, and compliance.
Connects Cybersecurity Initiatives to Strategic Business Goals
Hoshin Kanri starts by defining top-level objectives (e.g., growth, customer trust, compliance) and then cascades those into departmental and operational goals. Cybersecurity strategies are developed in direct support of these business priorities, rather than in isolation. Example: If the company goal is to expand into new markets, the cybersecurity strategy may prioritize compliance readiness (e.g., GDPR, HIPAA) and securing new supply chain relationships.
Creates a Clear, Cascading Deployment Plan
Cybersecurity goals are translated into measurable targets and initiatives at every level— from executive leadership to the SOC.This ensures vertical alignment and clarity: everyone knows how their actions contribute to strategic outcomes. Example: A company-wide objective to reduce operational risk is supported by cybersecurity objectives like reducing patch cycle time, decreasing MTTR, and automating access reviews.
Establishes Accountability and Cross-Functional Coordination
Hoshin Kanri uses a “catchball” process, where goals and plans are discussed, refined, and accepted across levels. Cybersecurity leaders work collaboratively with IT, legal, HR, and operations to build aligned, realistic plans with shared ownership. Example: The security team works with HR to roll out new user access controls as part of a broader resilience strategy.
Focuses on What Matters Most
By using tools like the X-Matrix, Hoshin Kanri helps teams prioritize high-impact initiatives that drive strategic outcomes, not just tactical wins. It prevents teams from spreading resources too thin across low-value projects. Example: Instead of launching multiple disconnected tools, a prioritized focus is placed on securing customer data and improving incident detection tied to SLAs.
Enables Ongoing Review and Course Correction
Hoshin Kanri includes regular review cycles (monthly, quarterly) to evaluate progress and adapt cybersecurity efforts based on new threats or business shifts. This builds agility into long-term planning—without losing alignment. Example: A spike in ransomware threats prompts a shift in investment toward endpoint resilience, without deviating from the overarching business objective of operational continuity.
By integrating Continuous Improvement methodologies, IT departments can develop adaptive security processes that evolve alongside emerging threats. The iterative, data- driven nature of CI enhances both proactive defense and reactive response, ensuring IT teams stay resilient in the face of dynamic cybersecurity challenges. Investing in CI tools ensures stronger security practices, reduced incident response times, and enhanced collaboration, ultimately protecting organizational assets and reputation.
Action Plan for Implementing Continuous Improvement in Cybersecurity
Assess Current Cybersecurity Practices
Develop Targeted Improvement Strategies
Implement Incremental Changes
Monitor and Measure Progress
Foster a Culture of Continuous Improvement
Align with Business Objectives
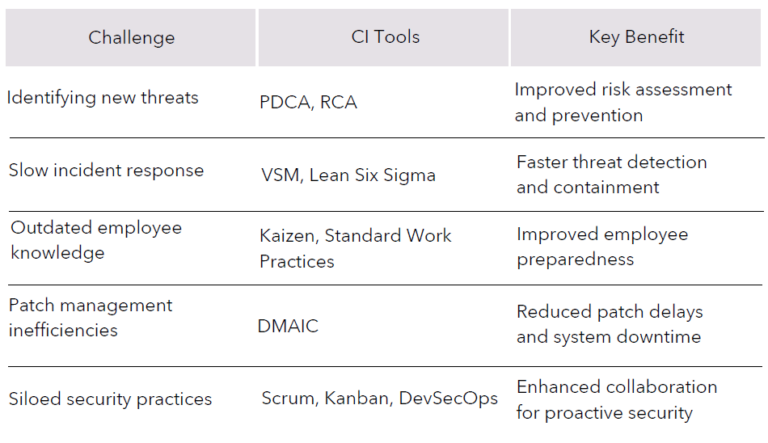
CI Tools for Cybersecurity Challenges
Start Your Continuous Improvement Journey
At Adonis Partners, our consultants are dedicated to helping you navigate this journey with expertise and precision. Discover how Adonis’ tailored solutions can support your initiatives to exceed goals, drive sustainable value, and transform your organization.
Get in touch with our team today.